Last month Opera announced it would be abandoning the Presto rendering engine that has been the basis of the browser since its inception. Instead the company will use the WebKit rendering engine for all its future releases, starting with this Opera Mobile for Android beta.
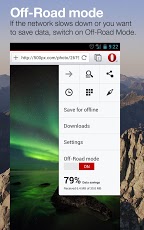
The revamped Opera for Android isn’t just different under the hood, Opera has redesigned the entire browser from the ground up opting for a more Android-native look. The new user interface is cleaner and reminiscent of Chrome for Android with a single menu button at the top of the screen rather than the space-eating toolbar found in the old Opera Mobile. While I prefer the new UI, it’s worth noting that the new design is decidedly less thumb-friendly.
Other cosmetic changes include combining the URL bar and search bar, and a new tab switching interface also similar to what you’ll find in Safari on iOS.
However, while the first WebKit-based Opera Mobile is clearly different it manages to retain, and even improve on, much of what made (makes) Opera unique.
For example, Opera Mobile’s trademark “Speed Dial” page
READ MORE: Reborn Opera Mobile Sings on Android | Webmonkey | Wired.com.