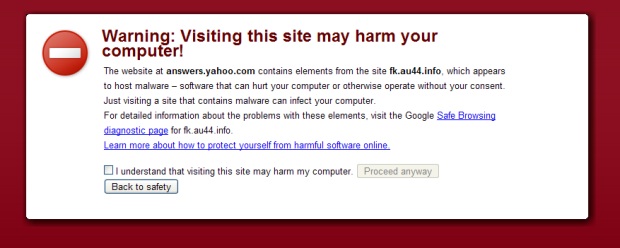
Security researchers have uncovered an ongoing and widespread attack that causes sites running three of the Internet’s most popular Web servers to push potent malware exploits on visitors.
Linux/Cdorked.A, as the malicious backdoor behind the attacks is known, has been observed infecting at least 400 Web servers, 50 of them from the Alexa top 100,000 ranking, researchers from antivirus provider Eset said. The backdoor infects sites running the Apache, nginx, and Lighttpd Web servers and has already exposed almost 100,000 end users running Eset software to attack (the AV apps protect them from infection). Because Eset sees only a small percentage of overall Internet users, the actual number of people affected is presumed to be much higher.
“This is the first time I’ve seen an attack that will actually target different Web servers, meaning the attacker is willing to create the backdoor for Apache, Lightttp, and nginx,” Pierre-Marc Bureau, Eset’s security intelligence program manager, told Ars. “Somebody is running an operation that can victimize various Web servers and in my opinion this is the first time that has ever happened. This is a stealthy, sophisticated, and streamlined distribution mechanism for getting malware on end users computers.”
Previously, Cdorked was known to infect only sites that ran on Apache, which remains by far the Internet’s most popular Web server application.
MORE: Attack hitting Apache sites goes mainstream, hacks nginx, Lighttpd, too | Ars Technica.