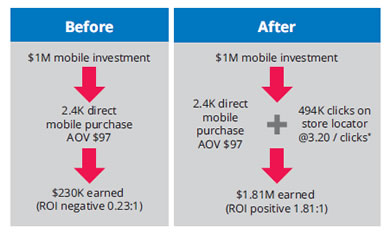
Recently, we reported that videos uploaded via Facebook have a higher Engagement Rate than YouTube links. You asked us how these two methods of uploading videos affect their reach – here are the results!
For the purpose of this study, we have chosen videos that brands have shared across Facebook during the last three months. As you know, there are two options – to either upload the video natively from your computer or to share a link to your video from YouTube. Apparently, admins prefer the latter, with 4 731 YouTube links posted vs. 554 Facebook videos, from December 4th – March 3rd 2013.
Facebook videos tend to have a higher Engagement Rate than YouTube links (0.22% on average compared to 0.10%). As already mentioned in the previous study, this could be due to the fact that you can play Facebook videos directly from the mobile news feed, which is increasingly becoming a preferred way of social update consumption. Interestingly enough, both YouTube links and Facebook videos generate nearly the same fan interaction, with about 77% of Likes, 16% of Shares, and 7% of Comments.
READ MORE: Facebook Videos Have a 10x Higher Viral Reach than YouTube Links